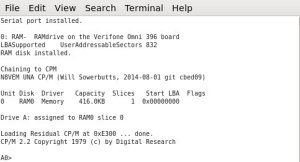
The Mark IV project has an SD card slot available as part of the design. The designer used the SIO (clocked serial I/O) port of the Z180, which allowed users to connect directly to the I/O pins of the SD card installed on their board. A bit of logic for card detection and selection and they have mass storage available.
I wondered if the same thing could be done with the credit card reader. I carefully traced the SIO pins on the credit card terminal, and found that only the receive line was connected. As should be done in good designs, the designers connected the input pin to ground. I needed one more pin to select the MicroSD card, ensuring that I could properly communicate with it. I continued my search tracing various pins on the board and found one that looked promising.
Along with the Z180, the credit card terminal uses a Zilog KIO, which supplies it with an extra pair of serial ports. I discovered that one of the output control signals was not being used and could be used as the MicroSD card’s select signal.
I purchased the appropriate adapter board for the MicroSD card, ensuring that the correct voltage level shifters were installed. Then, I carefully cut the one trace on the board, and soldered the required leads to the adapter.
With a slight adaptation of the UNA BIOS initialization routines, the firmware was now correctly accessing a MicroSD card.
My CP/M credit card terminal system now had 512MB of additional storage!